Several strategies are used to secure the security of the Virtual Private Server. Some of the more critical methods are website isolation, root access, and third-party security programmes.
This article examines how server virtualization using a hypervisor accomplishes just that.
What is a Hypervisor for VPS Security?
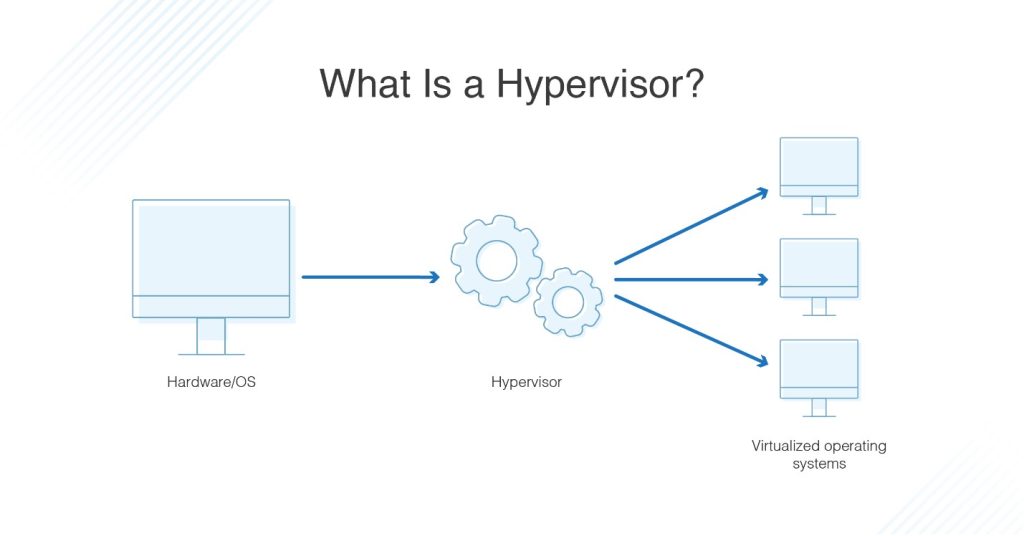
A hypervisor is a piece of hardware, software, or a combination that sits on a server and generates VMs (Virtual Machines).
A server contains numerous VMs, and each VM consumes resources from the server. The server’s resources are exclusive to each VM and cannot be shared. Each VM, however, is independent of the other VMs on the server. They are also completely cut off from one another. The hypervisor handles all of this.
Each VM in a hosting configuration is a website. The idea, of course, is that each website has its own set of resources and that each website is separated from the others.
When it comes to security, this architecture provides various advantages. Some of the most important are listed here.
Benefits of Hypervisors and Virtualisation for Security
1. Isolation limits your vulnerability to risk
Isolation of VMs and thus websites is a big benefit to website security. When a website is isolated from the other websites on the server, the security configuration of the other websites is made ineffective.
In hosting solutions that do not provide isolation, if one website has bad security, it might have a negative impact on all of the other websites. This problem, however, is eliminated when websites are segregated. So, with a VPS system, if a website is successfully attacked, just that website is harmed.
2. Allowance for the usage of third-party applications
As websites grow in size, so do the risks, because they typically contain more client data. You can install server-wide third-party programmes with VPS Hosting even if they are not natively supported by your hosting provider.
There are a plethora of cloud-based security technologies available nowadays that can effectively safeguard your website. However, you cannot always use them in a hosting environment that does not provide website isolation. This occurs as a result of an application placed on one website having an impact on the user experience of other website owners.
Because of the isolation provided by virtualisation and hypervisors, hosting providers can allow consumers to run whatever apps they wish. This manner, if a security application can benefit your website, you can install it without having to wait for your hosting company to approve it.
3. Root access is provided by hypervisros
In a Linux system, root access is quite similar to ‘Admin’ access in a PC. A root user, in essence, has the greatest level of access and can make any changes to the system.
One of the most critical security benefits of a VPS is root access, which is made possible through virtualization. You can manage ports, install or delete programmes, adjust the JavaScript delivery, and do a lot more with root access.
If there is no isolation, root access is not possible. Because root access allows you to change extremely basic features of your system, it is not available when there is no isolation. With root access, you have the ability to make modifications that may have a negative impact on other websites on the server.
However, the hypervisor enables virtualisation and, as a result, total isolation of websites, allowing hosting firms to provide root access with their VPS Hosting plans.
Having root access has various security benefits. To begin, it allows you to control your ports. A port is essentially a channel that allows the server to speak with the outside world. Unfortunately, unused ports might become targets for hackers.
You can block any unused ports with root access, preventing hackers from exploiting them. You can also change port numbers if you have root access. This is significant due to the genuinely scary volume of bot attacks on servers.
A bot attack occurs when a ‘bot’ or a malicious piece of software accesses your servers. Hacker-created bots are now capable of carrying out a full-fledged attack on a system with no human participation. One of the causes of this issue is that many website owners leave their port numbers unaltered. As a result, many servers become similar targets.
You can switch and modify port numbers with root access, reducing the risk of bot assaults on your website.
4. Virtual machines can be 'rolled back.'
One of the benefits of virtualization is the ability to roll back VMs. For example, if a VM becomes infected for whatever reason, it may simply be rolled back to its pre-infection state.
Of course, the benefit is self-evident. If the hack was successful, the website can be returned to its previous state. Furthermore, it is not only hackers who can mistakenly alter a website. Technical flaws can also occur.
The virtualisation-enabled rollback option means that you can always roll back your website to a point when everything was at its best.
Conclusion
VPS hosting is becoming increasingly popular, and for good reason. VPS hosting offers dedicated hosting-like performance at a fraction of the cost. Furthermore, the security provided by virtualization, root access, and the hypervisor ensures that VPS security is on par with dedicated hosting.
Of course, selecting the correct web hosting service is critical. A good web hosting firm would invest a significant amount of money and skill in providing safe, dependable, and speedy VPS Hosting. They employ additional firewalls, hire professionals with years of knowledge, and employ security solutions to ensure that your VPS-powered website is always secure.

